Most Azure Policy rollouts don’t fail because the policy JSON is wrong. They fail because the process is wrong.
If you’ve ever pushed a "simple" initiative update and triggered a flood of noncompliance, broken deployments, or an exception stampede, you’ve seen the pattern: policy changes behave like production changes.
So treat them that way. Policy-as-code is not a folder in a repo. It’s a workflow with gates, traceability, and a rollout plan.
The outcome you want
A policy workflow that:
· catches bad changes before they hit broad scope
· forces clarity on intent, impact, and blast radius
· supports time-bound exemptions without turning into policy theater
· rolls out in rings with an escape hatch
· leaves evidence for audit and leadership questions
Why PR gates matter for policy
Azure Policy isn’t just governance. It’s a control plane that can block deployments, trigger remediation, and change what “allowed” means for every team downstream. That’s why the pipeline needs to answer three questions on every change:
· Is the change valid (schema, parameters, references)?
· Is the change safe (scoped, staged, reversible)?
· Is the change explainable (who approved it, why, and what’s the expected impact)?
A good PR gate doesn’t slow teams down. It makes risk visible early, so you don’t pay for it later in incident calls and exception backlogs.

Design the repo like a product
Start with a repo that makes intent obvious. The structure below is boring, and that’s the point:
repo/
initiatives/
landing-zone-baseline/
initiative.json
parameters.json
README.md
definitions/
deny-public-ip/
policy.json
parameters.json
README.md
exemptions/
prod/
2026-02-15-appteam-blob-public-access.json
assignments/
rings/
dev.json
pilot.json
prod.json
pipelines/
azure-pipelines.yml
docs/
rollout-playbook.md
rbac-model.md
Keep each policy/initiative self-contained with a README that answers the following questions: what it enforces, why it exists, and how teams comply. If a control can’t be explained in plain language, it will create friction.
PR gates: the minimum set that prevents pain
You can build a ton of automation here, but you don’t need to start fancy. The minimum set below catches most failures and forces good review conversations.
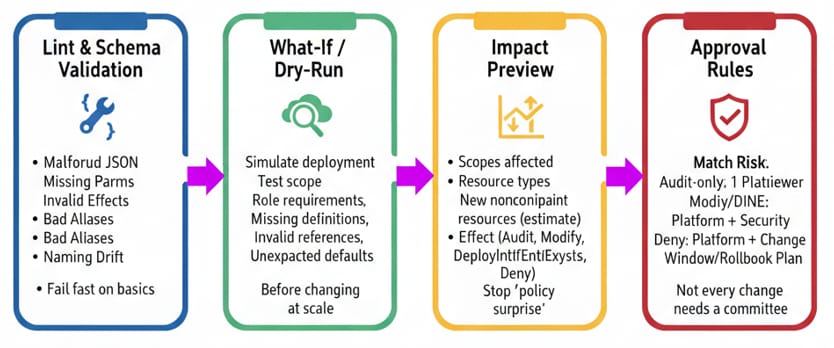
Gate 1: Lint and schema validation
Fail fast on the basics: malformed JSON, missing parameters, invalid effects, bad aliases, and naming drift. Treat this like a compilation step for policy.
Gate 2: What-if / dry-run at the target scope
Before you change policy at scale, simulate the deployment. In Azure DevOps or GitHub Actions, run an "incremental" deployment with what-if enabled against a test scope. The goal is not perfection. It’s catching surprises: role requirements, missing definitions, invalid references, and unexpected parameter defaults.
Gate 3: Impact preview
If your PR can’t answer “what will change,” it shouldn’t merge. Include an impact section that describes:
· Which scopes are affected (management group, subscription, resource group)
· Which resource types are in play (VMs, Key Vaults, Private Endpoints, etc.)
· Expected new noncompliant resources (rough estimate is fine)
· Whether the effect is Audit, Modify, DeployIfNotExists, or Deny
This is where you stop "policy surprise". Even a manual estimate is better than merging blind.
Gate 4: Approval rules that match risk
Not every policy change needs a committee. But Deny and auto-remediation changes should have stronger review than an Audit policy tweak. A simple model:
· Audit-only changes: 1 platform reviewer
· Modify / DeployIfNotExists: platform + security signoff (or delegated reviewer)
· Deny: platform + security + a change window (or a documented rollback plan)
Exemptions: stop pretending you can eliminate them
Exemptions are not failure. Unmanaged exemptions are a failure.
You want an exemption workflow that’s predictable and time-bound, with clear owners and expiration dates. The fastest way to get there is to manage exemptions as code, in the same repo, under PR control.
What an exemption needs (every time)
· Scope: exactly where the exemption applies (resource, RG, subscription)
· Policy reference: which definition or initiative item is being exempted
· Reason: plain language, not "business need"
· Owner: a person/team who will remove it
· Expiry: a date, always
· Ticket link: the work item that tracks remediation or migration
If you’re missing expiry, you’re not granting an exemption. You’re creating a permanent loophole.
Rollout safety: rings, not big-bang
The best policy rollout is the one nobody notices.
Use a ring model so you can validate behavior on a small, representative set of subscriptions before broad scope. A practical ring pattern:
· Ring 0 (dev): sandbox subscriptions and policy lab scopes
· Ring 1 (pilot): 1-3 real subscriptions with friendly teams
· Ring 2 (prod): management group or full subscription fleet
Pair rings with effect staging. Start with Audit, then move to Modify/DeployIfNotExists, and only then consider Deny. That gives teams time to fix drift before you block deployments.
A rollout playbook that won’t melt ops
Here’s a process I’ve seen work in real environments with lots of subscriptions and lots of competing priorities:
1. Create or update the definition/initiative in a feature branch.
2. PR must include: intent, impact preview, ring target, and rollback plan.
3. Pipeline runs: lint + what-if + deployment to Ring 0.
4. Merge triggers: Ring 1 assignment update (pilot).
5. Observe for a fixed window (example: 7-14 days): compliance trend, deployment failures, exemption requests.
6. If stable, promote assignment to Ring 2 (prod).
7. If not stable, roll back the assignment or revert the PR. Do not "hotfix" policy in the portal.
Make it observable
If you can’t see compliance drift and exemption volume, you’ll always feel behind. Add two signals to your operating rhythm:
· Compliance trend by initiative and by ring (daily is fine)
· Exception volume: new exemptions created per week, and exemptions expiring in the next 30 days
Those two charts will tell you whether your policy program is improving behavior or just generating noise.
What to put in your PR template
If you do nothing else, add a PR template. It forces the right conversations without adding meetings. Suggested sections:
· Change summary (1-3 sentences)
· Policy type (definition vs initiative) + effect(s)
· Scope + ring target (dev/pilot/prod)
· Impact preview (what changes and who feels it)
· Exemptions needed (if any) + expiry plan
· Rollback plan (how to unwind safely)
Common failure modes (and how this workflow prevents them)
Failure mode | Countermeasure |
"It worked in the portal" change breaks at scale | Lint + what-if catches missing roles, bad parameters, and deployment diffs. |
Deny goes live and blocks releases | Ring rollout + effect staging limits blast radius and forces a rollback plan. |
Exemptions become permanent | Exemptions-as-code with expiry and owner makes drift visible and reversible. |
Every policy change becomes a debate | PR template makes the why and impact explicit, so reviews stay grounded. |
If you already have policy deployment in place, start small: add the PR template and ring model first. That one change tends to reduce surprise the fastest.
Want my Azure DevOps policy-as-code checklist?
Get it Here and I’ll send you the ADO checklist that covers:
· repo layout + naming conventions
· PR template fields that force clarity
· recommended gates (lint, what-if, ring deploy)
· exemption workflow with expiry + ownership
· rollout rings + effect staging

Next steps
Pick one of these for your next iteration:
· Add a PR template and enforce it for all policy changes.
· Stand up Ring 0 and Ring 1 assignments so you can pilot safely.
· Move exemptions into code with expiry and owners, even if the process is manual at first.
When your policy program feels calm and predictable, teams stop fighting it and start relying on it. That’s the goal.