If your org is still arguing about moving fast versus being safe, you're stuck in a false choice.
High-performing cloud teams do both. Not by writing longer standards. Not by adding more approvals. They do it by building guardrails that match risk, and rolling them out in a way that respects delivery flow.
Most guardrails fail for three predictable reasons:
· They show up late (right before release).
· They feel arbitrary (nobody can explain the why in plain language).
· They have no escape hatch (so teams work around them).
Here's the model I use to avoid all three: a three-level guardrail ladder. It works in Azure, but it's not Azure-specific. It's an operating pattern.
What a guardrail is (and what it is not)
A guardrail is a constraint that prevents avoidable damage while keeping the delivery intact. It should reduce risk and reduce surprise.
A guardrail is not:
· A surprise "deny" policy that appears the day before go-live
· A ticket gate that turns platform teams into human middleware
· A standards PDF that nobody reads until after the incident
Good guardrails behave like good operations:
· Clear intent
· Predictable outcomes
· Fast feedback
· Measurable impact
The 3-level guardrail ladder
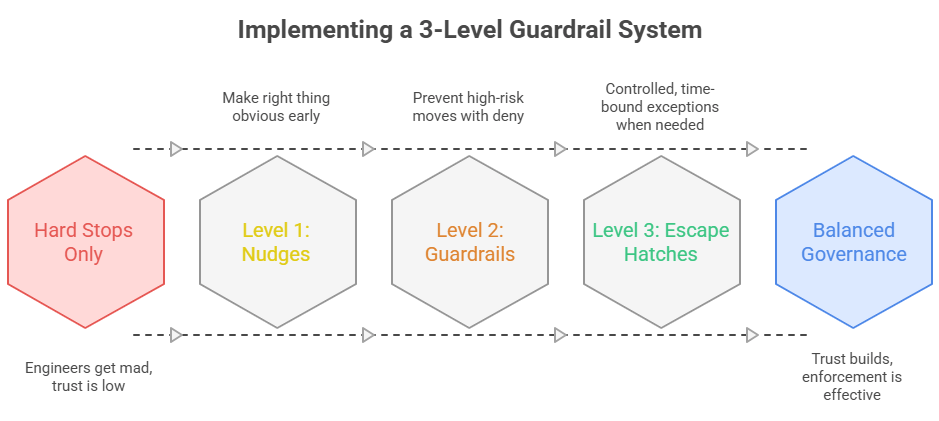
Think of guardrails as a ladder. Most orgs skip Level 1 and jump straight to hard stops. That's why engineers get mad. The ladder builds trust first, then adds enforcement where it actually matters.
Level 1: Nudges (visibility + fast feedback) 👀
Goal: make the right thing obvious, early. This level should feel helpful, not punitive.
What it looks like in practice:
· Policies that audit and report (no blocking yet)
· CI checks that comment on a PR with "this will fail later unless you fix X"
· Dashboards that show compliance by team, not just a global percent
Examples (Azure-flavored, but portable):
· Missing required tags (owner, app, env, cost center)
· Public exposure signals on resources that should usually be private
· Non-standard SKUs flagged so teams see cost and support risk before they deploy
· Region drift visibility (especially helpful in large orgs)
Design rules for Level 1:
· If an engineer can't understand the rule in one sentence, rewrite it.
· Every nudge must include the fastest path to fix it.
Operator rule: A nudge without a clear fix is just noise.
Level 2: Guardrails (hard stops for high-risk moves) 🛑
Goal: prevent the moves that create a real blast radius. This is where deny belongs, but only for rules that meet all three tests.
Only block things that are:
· High blast radius if they go wrong
· Common mistakes that keep happening
· Easy to do safely because a paved road exists
Examples:
· Block public access to services that should never be internet-facing
· Restrict regions when residency requirements are non-negotiable
· Enforce encryption and baseline TLS settings in production
· Require production diagnostics and logging for critical workloads
Design rules for Level 2:
· Only block what you're willing to support with a paved road.
· Never roll out a hard stop without a clear alternative path.
· Start in non-prod, then production, then expand scope.
Operator rule: If you can't offer a paved road, don't ship a hard stop.
Level 3: Escape hatches (controlled, time-bound exceptions) 🔑
Goal: keep shipping when reality gets messy, without losing control. This is the level most orgs forget. Then exceptions turn into shadow IT or weekly bypass meetings.
Minimum escape hatch requirements:
· A clear owner (person or team)
· A written reason (plain language)
· A ticket ID or approval trail
· A hard expiry date (no forever exceptions)
· Logging that proves what happened
Examples:
· Temporary approval to deploy a non-standard SKU for a performance test
· Time-bound exception while a vendor product catches up
· Break-glass path for incident response, followed by review
Design rules for Level 3:
· Exceptions are normal. Untracked exceptions are failures.
· Your exception backlog tells you what guardrails need better paved roads.
The "don’t block shipping" design test
Before you add a guardrail, ask three questions:
1) What problem are we preventing? Be specific. “Security” is not a problem statement. “Public storage endpoints in production” is.
2) How often does it happen? If it's rare, Level 2 is usually overkill. Start with Level 1.
3) How fast can teams remediate it? If the fix takes longer than the release window, you'll create resentment and bypasses.
A simple heuristic I use:
· Reversible + low blast radius → Level 1
· Irreversible or high blast radius → Level 2
· Needed to ship but still risky → Level 3
How to roll this out without starting a war
Two patterns keep guardrails from turning into bureaucracy.
1) Observe, then enforce
Run Level 1 reporting long enough to learn what will break, which rules are noisy, and where teams need a paved road. Then promote the rule to Level 2 only when all of this is true:
· There is a clean remediation path
· False positives are low
· You can explain the why in one sentence
2) Paved roads matter more than policy text
If the safe path is harder than the unsafe path, the policy becomes a fight. Paved roads are the shortcuts that make the right thing the easy thing.
Good paved roads usually look like:
· Templates or modules engineers already use
· Secure and cost-aware defaults baked into those templates
· PR checks that catch issues before deployment, not after
Measure impact like an operator
If you can't measure it, you can't defend it. The metrics that actually help:
· Compliance by team (not just overall)
· Mean time to remediate (how long issues live)
· Exception count and average age (how long exceptions stick around)
· Top rules creating friction
· Lead time trends (make sure guardrails aren't quietly slowing delivery)

A practical starter pack (works in most Azure orgs)
If you're building this from scratch, here's a clean set that usually lands well. It's enough control to reduce risk without turning the platform team into the no team.
Level 1: Nudges
· Required tags: owner, app, env, cost center
· Public exposure flags
· Non-standard SKUs flagged (cost and support risk)
· Region drift visibility
Level 2: Hard stops
· No public endpoints for sensitive services in production
· Approved regions only (when required)
· Encryption and TLS baselines enforced
· Production diagnostics/logging required
Level 3: Escape hatch
· Ticketed exception workflow
· Auto-expiry and review
· Logged approvals
· Exception reporting by team
If you have 30 minutes this week
Do this once, and you'll immediately see where your guardrails should start:
1. Pick one high-risk rule you wish you had (one sentence).
2. Implement it as a Level 1 audit-only for 2–4 weeks.
3. Track the top 3 failure modes and the top 3 teams affected.
4. Build or fix the paved road (template/defaults) for the safe path.
5. Then promote it to Level 2 in non-prod first.

Time to Act!
Want the Guardrail Ladder template (Levels 1–3, rollout checklist, and a clean exception workflow)? Grab it here —> https://tally.so/r/OD7XOp